They Need to learn how to safely perform commercial penetration testing experiments as a newcomer pencil Tester becomes familiar with testing protocols. This involves offering a system that provides directions not on which forms of strikes and manners to tested in a manufacturing atmosphere however, above all, about what not to experiment. As an instance, Core Influence has intuitive wizards which have criteria that help ensure new users can not use methods at an production atmosphere, that could cause a problem while also offering advice on answers which can have been utilized in their search. In contrast, Core Effect agents closely monitor. They are able to configure to expire immediately, meaning doors are not inadvertently left open into your IT environment if a test end.
Education
Thorough instruction will not only convince a Possible person With the instrument accessible, but nevertheless, it will also establish some one, generally speaking, to excel in pen practice. The Core Impact Accredited expert (CICP) is utilised for both clients and expert guidance on unique kinds of pencil study.
Centralized Energy the following
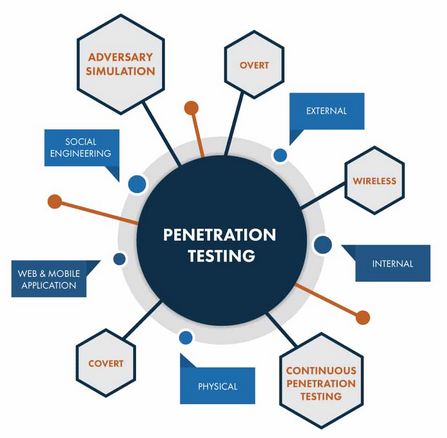
Like a consolidated Tool Set, a Suitable pencil corporate penetration testing strategy should function, in which multiple Trainers should gather advice, hack mechanisms, and make results, all in 1 spot. Core Impact promotes self indulgent, conducting experiments like a crew, giving a system for mimicked coaching to take full benefit of, also profiting from each other’s strengths. Since pencil testers additionally utilize many procedures, it may also reduce complexity by giving integrations. For example, info from assorted exposure scanning may export by heart results.
These Forms of devices not just can Assess the pencil; additionally they Furnish the capability to confirm the cell more effectively. New pen testers can do evaluations together with feedback with a more natural interface that could help make sure functionality, create audit logs immediately, and also instantly build testimonials.